There are 1001 ways to hack a WordPress site and Shield Security eliminates a massive chunk of them.
The Shield Security plugin for WordPress is introducing a new file security bouncer – it will detect, and automatically eliminate, any files on your WordPress site that don’t belong.
This article will discuss what this new feature gives you, how it does it, and how you can better protect your site with the latest Shield Security plugin.
Remember the trusty Core File Scanner?
Some time ago we introduced the Core File scanner that detects & repairs WordPress core files on your site.
It ensures that your core files are legitimate. That is, if we were to download the WordPress files from WordPress.org again, they would be identical in every way to what’s sitting on your web server.
This is an absolutely critical tool in the mitigation of WordPress security threats. Many hacks take the form of code injected into existing, legitimate files e.g. WordPress Core Files. Just looking at these files in a file manager isn’t enough to know that they’ve been altered in any way. You need to examine the contents of the files.
This is what the core file scanner protects against. It ensures that none of your core files contain code that shouldn’t be there.
This is great for files that we “know” about. But what about files that aren’t part of your WordPress installation?
The ‘Unrecognised File Scanner’ – Detects Files That Shouldn’t Be There
Until now we didn’t have a way to account for these. The new ‘Unrecognised File Scanner‘ handles this. (yea, we know, it isn’t the most glamorous name ever 😉 )
Using the same list of official files (as from the Core File Scanner) we identify files that aren’t on the list. Any non-standard files stored inside the WordPress core installation are simply in the wrong place.
Stop: Never store files in the core WordPress directories ‘wp-admin’ and ‘wp-includes’. Ever.
Assuming you keep to the rule above, you can safely delete anything that doesn’t belong there.
This scanner eliminates a whole swath of threats that sneak onto your website and sit there silently, undetected for months and maybe even years.
No Escape. No Exceptions. (well, except for a few)
The rule is: if the file isn’t part of WordPress core, it will be deleted.
But there are a couple of files you might have there which don’t ship with WordPress, namely:
error_log.htaccess.htpasswd.user.ini
We may extend this list as we receive feedback from clients, but for now those are the only non-standard files that will be permitted to stick around.
Not All Core Folders Are Scanned By Default?
By default, the scanner will only scan the full contents of the following directories:
wp-adminwp-includes
It will not scan wp-content since this is where all custom code and plugins/themes ought to go. And, it will not scan the top-level of your WordPress installation folder.
But, you have the ability to select these directories by using ‘File Scan Areas’ option.
Why the top-level WordPress installation folder is excluded from the scan by default
We are huge advocates of running WordPress installations within their own directory. If you remain unconvinced, then we recommend doing it to keep things organised and tidy, at the very least.
Since most admins don’t do this, we can’t allow the scanner to run on the top-level WordPress installation folder as this would also be the public HTML document root. If we did, it would likely delete many files that admins have placed there which are critical to the normal running of the site.
But, if you do keep WordPress in its own directory, we’ll be releasing a patch upgrade to handle this scenario shortly after our v5.12.0 release. We also suggest you leave a comment below about typical files you might like to see excluded – we will of course only include exclusions that make sense for everyone.
How to get the new scanner on your WordPress sites
As with all our core security features, this is a free feature on the Shield Security plugin, v5.12.0 onward.
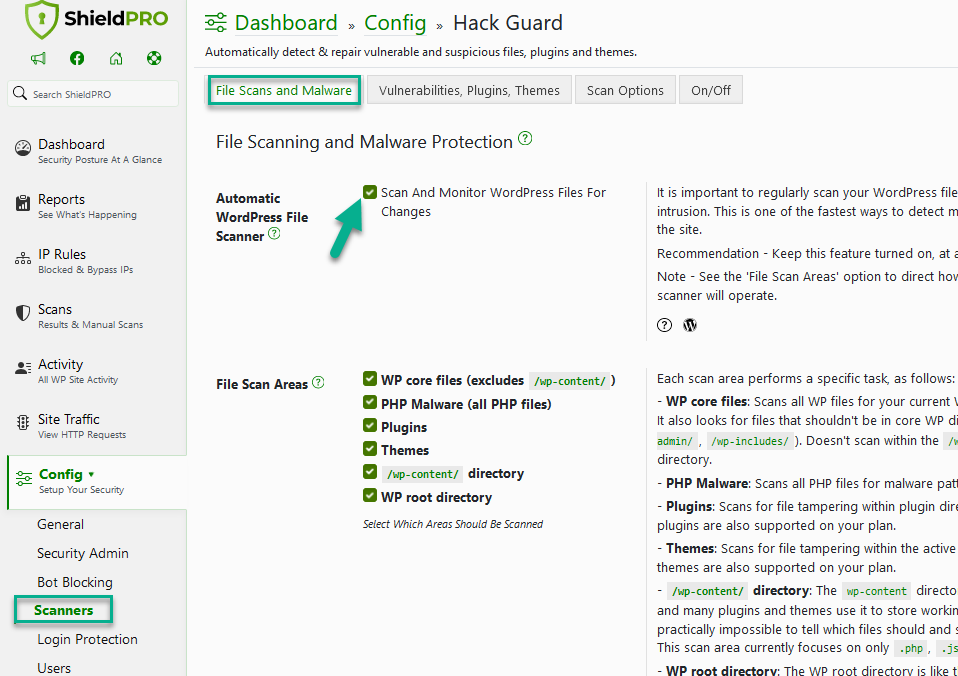
The feature is enabled by default and is a part of the Hack Guard module > Automatic WordPress File Scanner.
It runs automatically in the background using the WordPress cron system, and you can manually delete any unrecognised files that are discovered.
Shield Central – Turn On The Scanner For All Sites In Seconds
If you have more than a few sites to maintain, you can use Shield Central to switch on this feature across all your sites at once. The best way to achieve this is to update one of your Security Profiles and then push it out to your network.
Shield Central is built specially for cases just like this where you need to roll out new features quickly, and with no hassle.
Question and Comments?
This is a new feature and there’s every chance we’ve overlooked something, so please leave us your comments below and we’ll address all questions and concerns.
Thank you all, as always, for your support!
Hello dear reader!
If you want to level-up your WordPress security with ShieldPRO, click to get started today. (risk-free, with our no-quibble 14-day satisfaction promise!)
You'll get all PRO features, including AI Malware Scanning, WP Config File Protection, Plugin and Theme File Guard, import/export, exclusive customer support, and much, much more.
We'd be honoured to have you as a member, and look forward to serving you during your journey towards powerful, WordPress security.
ShieldPRO Testimonials
Comments (24)
Leave a Comment
Main Sections
- Remember the trusty Core File Scanner?
- The ‘Unrecognised File Scanner’ – Detects Files That Shouldn’t Be There
- No Escape. No Exceptions. (well, except for a few)
- Not All Core Folders Are Scanned By Default?
- Why the top-level WordPress installation folder is excluded from the scan by default
- How to get the new scanner on your WordPress sites
- Shield Central – Turn On The Scanner For All Sites In Seconds
- Question and Comments?





Sounds good to me.
Just FYI since we have full control over our entire environment, cloud servers, network etc, we run Linux Malware Detect (Maldet) to scan not just the WordPress files mention but all files/directories.
Any issue with the two working together (Shield Central Scanning and Maldet)? I am thinking not, but wanted to ask anyway.
Thanks for the great work you and your team does Paul.
Hi Roy,
Great to hear you have something in-place there on your servers already. We can’t see any issue in conflicting between the two systems, but of course, if you spot something please let us know asap.
Thanks! 🙂
Paul.
Please exclude also Web.config (correspond to .htaccess but for IIS servers).
Cool, got it, thanks!
Thanks to you.
Unfortunately on IIS server under Windows it detect all files as unrecognized.
See:
[QUOTE]Shield detected files on your site which are not recognised.
This is part of the Hack Protection module for the WordPress Unrecognised File Scanner.
…
The following files do not match the official WordPress.org Core Files:
– D:\inetpub\webs\mysitenameycom/wp-admin\about.php
– D:\inetpub\webs\mysitenameycom/wp-admin\admin-ajax.php
– D:\inetpub\webs\mysitenameycom/wp-admin\admin-footer.php
– D:\inetpub\webs\mysitenameycom/wp-admin\admin-functions.php
– D:\inetpub\webs\mysitenameycom/wp-admin\admin-header.php
– D:\inetpub\webs\mysitenameycom/wp-admin\admin-post.php
– D:\inetpub\webs\mysitenameycom/wp-admin\admin.php
…
[/QUOTE]
Windows being Windows – We should be able to account for this – we’ll get an update out asap. Thanks for reporting this!
It works now, thanks.
But is it possible to uniform the behaviour?
It is fine on Windows whether is slash or backslash (both are working) but it would be nice to not have both together.
Now on the e-mail it is showed like this:
– D:\inetpub\webs\mysitenamecom/wp-admin\test.php
That path output is just a cosmetic issue. We may look at that, but more importantly it’s operating as expected.
Glad to hear it’s working as expected.
Thanks for reporting back!
Hi,
it would be nice to have a button “Scan now” for both Core File Scanner and Unrecognised Files Scanner.
It is annoying waiting one day to test it.
Also running the cron job forcedly doesn’t seem to work.
On-demand scanning for the Core File Scanner is, amongst other things, available through Shield Central within iControlWP.
We will probably also provide the ability through a Pro version of the Shield plugin at a later date.
Thanks for your feedback!
I am clearly not a web wizard and have no idea where these files came from or what they do. Is it safe for me to let the file scanner resolve the list below? What are my option if something breaks?
The following files do not match the official WordPress.org Core Files:
– /hermes/bosnaweb17a/b639/ipg.douglasw/wp-admin/includes/class-wp-menu.php
– /hermes/bosnaweb17a/b639/ipg.douglasw/wp-admin/options-option.php
– /hermes/bosnaweb17a/b639/ipg.douglasw/wp-includes/default-menu.php
– /hermes/bosnaweb17a/b639/ipg.douglasw/wp-includes/theme-compat/archive.php
Hi Douglas!
You should always have a backup handy for your sites.
But if you’re curious, you should download the WordPress installation files for your current version, whichever that is, and check whether these files really exist. If they don’t, then you shouldn’t need them and you should delete the files from your site.
I did a quick check for WordPress 4.8 and those files don’t belong.
Links
A solid backup system – https://www.icontrolwp.com/sign-up/
WordPress Release Archive (so you can find what files you should have) – https://wordpress.org/download/release-archive/
Thanks!
Paul.
Hi Paul, thanks for this feature. Haven’t had a chance to look at it, but, if not present already, maybe a user-editable textarea for an additional exclude list would be helpful?
Other candidates for the standard exclude list:
.htaccess* (for backups/tests)
user.ini (without leading dot)
/piwik/ (for the top-level scanner)
Also:
google*.html (for site verification)
This file sometimes appear on wp-admin folder, at least for siteground cpanel installs:
php_errorlog
Thanks!
With the latest release next week, you’ll be able to add your own custom exclusion files.
Thanks for this wonderful guide. I like your article it was very helpful. Keep sharing
Hello,
I have started to receive your auto-emails: Warning – Unrecognised WordPress Files(s) Detected…
..informing me of a file in the wp-admin folder called ht.txt of which looks identical to .htaccess
I have also noticed .htaccess is located in both the public_html AND wp-admin folders. Strange. No doubt you will advise deleting the latter?
Thanks 🙂
Hi,
We unfortunately can’t advise with any particular cases as we have no idea as to what your website requires. .htaccess files are perfectly legitimate in any folder.
Our position for our sites, is that any files in the core folders not of WordPress or required by the hosting, e.g. .htaccess etc. should be removed.
If you have any doubts, contact your host/website dev.
Thanks!
As cybercrime is getting higher then this is so important to give much attention to your security. your blog is full of such information. and this will help who are starting their business online or with new sites.
We can not see any issue in the conflict between the two systems, No doubt it is good to a blog which provides the best solution to eliminate Hacker Files.
Very useful information for everyone. I getting full knowledge after reading this information. Keep updating this kind of information. I am your regular reader.
This is really a great guide, because it’s very essential to eliminate the hacker because of it’s the issue of every user security . I support the steps.